Aws S3 Security Whitepaper

Amazon web services aws is a flexible cost effective easy to use cloud computing platform.
Aws s3 security whitepaper. This whitepaper is designed to help architects and developers understand the different storage services and features available in the aws cloud. The aws security whitepaper covers aws s general security controls and service specific security. How security responsibilities. The whitepaper also provides an overview of.
To operate your workload securely you must apply overarching best practices to every area of security. For more information about additional measures you can take refer to the aws security best practices whitepaper and recommended reading on the aws security learning webpage. We have just published an updated version of our aws security best practices whitepaper. Staying up to date with aws and industry recommendations and threat intelligence helps you evolve your threat model and control.
Aws storage services overview aws whitepaper usage patterns amazon s3 amazon simple storage service amazon s3 provides developers and it teams secure durable highly scalable object storage at a very low cost. We provide an overview of each storage service or feature and. It provides security best practices that will help you define your information security management system isms and build a set of security policies and processes for your organization so you can protect your data and assets in the aws cloud. Aws whitepapers guides expand your knowledge of the cloud with aws technical content authored by aws and the aws community including technical whitepapers technical guides reference material and reference architecture diagrams.
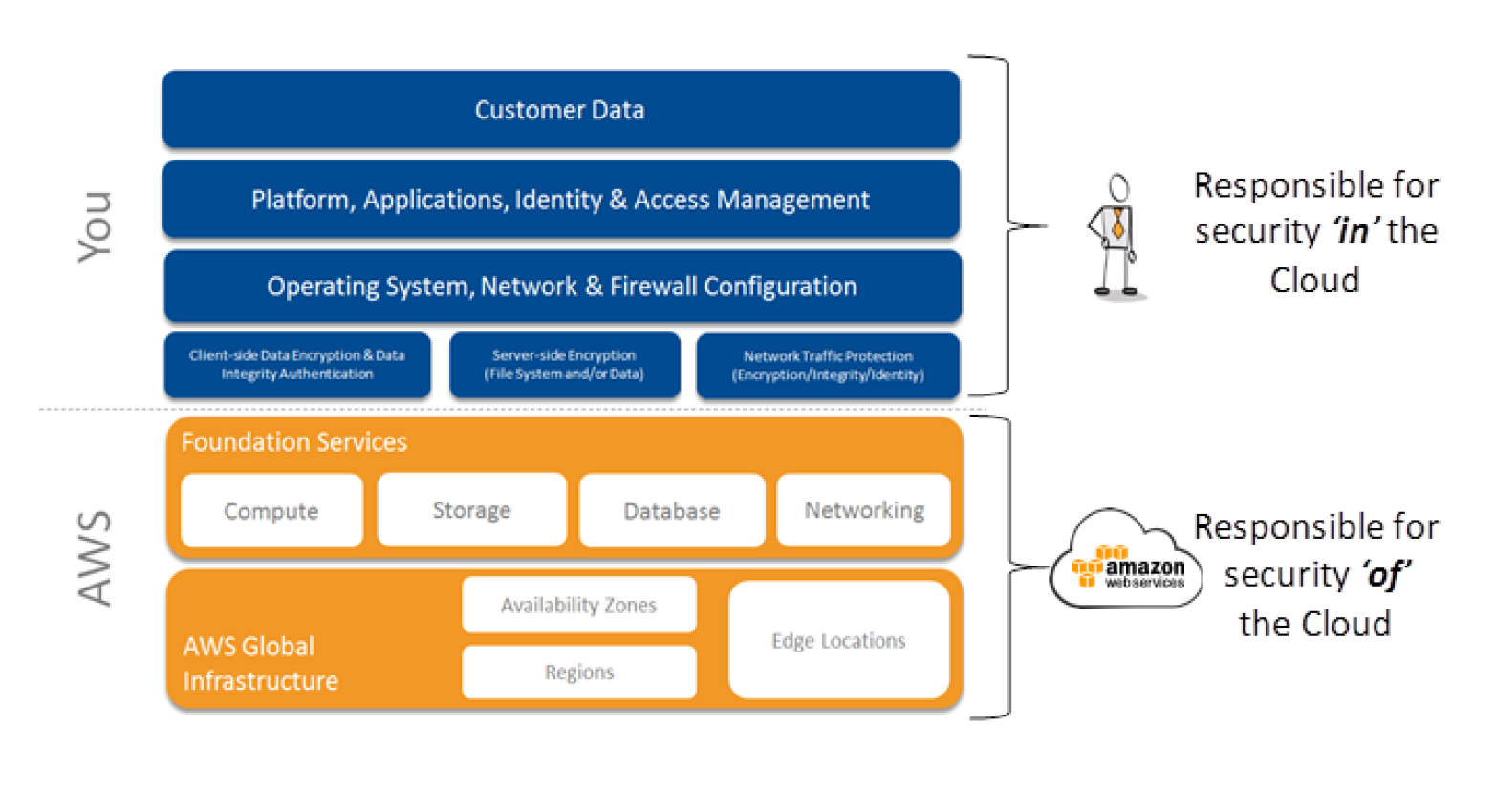
Specifically you asked for. Overview of security processes aws whitepaper aws security responsibilities shared security responsibility model before covering the details of how aws secures its resources it is important to understand how security in the cloud is slightly different than security in your on premises data centers. Shared responsibility environment moving it infrastructure to aws services creates a model of shared responsibility between the customer and aws. You wanted us to provide a holistic and familiar approach to managing the overall information security posture of the organization that s based on periodic risk assessments when you deploy applications and assets on aws.
Take requirements and processes that you have defined in operational excellence at an organizational and workload level and apply them to all areas. In amazon web services aws.